IEC 27001 Information Security Management System
ISO/IEC 27001 is the world’s most popular standard for information security management, and certification to this standard is highly sought after. It demonstrates an organization’s ability to safeguard information with robust controls, ensuring trust and reliability.
Overview
ISO/IEC 27001 Information Security Management System – Training Courses
Learn how to build your expertise in ISO/IEC 27001, the international standard for Information Security Management Systems (ISMS). Whether you’re starting your journey or advancing your career, our ISO/IEC 27001 training courses and certifications equip you with practical, in-demand skills to protect data, manage information risks, and enhance digital trust.
What is ISO/IEC 27001?
ISO/IEC 27001 provides requirements for organizations seeking to establish, implement, maintain and continually improve an information security management system. This framework serves as a guideline towards continually reviewing the safety of your information, which will exemplify reliability and add value to services of your organization.
Why is ISO/IEC 27001 important?
ISO/IEC 27001 assists you to understand the practical approaches that are involved in the implementation of an Information Security Management System that preserves the confidentiality, integrity, and availability of information by applying a risk management process. Therefore, implementation of an information security management system that complies with all requirements of ISO/IEC 27001 enables your organizations to assess and treat information security risks that they face.
Certified ISO/IEC 27001 individuals will prove that they possess the necessary expertise to support organizations implement information security policies and procedures tailored to the organization’s needs and promote continual improvement of the management system and organizations operations.
Moreover, you will be able to demonstrate that you have the necessary skills to support the process of integrating the information security management system into the organization’s processes and ensure that the intended outcomes are achieved.
ISO/IEC 27001 Requirements and Controls?
Key Requirements of ISO/IEC 27001
ISO/IEC 27001 outlines several mandatory requirements that ensure a systematic approach to managing sensitive information. The most important requirements include:
- Context of the Organization
- Identify internal and external issues affecting information security.
- Determine the needs and expectations of stakeholders.
- Leadership and Commitment
- Top management must demonstrate active involvement in ISMS implementation.
- Establish clear roles, responsibilities, and policies.
- Risk Assessment and Risk Treatment
- Identify, analyze, and evaluate risks to information security.
- Implement appropriate risk treatments to mitigate identified risks.
- Support
- Provide adequate resources, training, and communication to ensure ISMS effectiveness.
- Operation
- Plan, implement, and control ISMS processes.
- Manage risks and security incidents effectively.
- Performance Evaluation
- Conduct internal audits and management reviews to evaluate ISMS performance.
- Continual Improvement
ISO/IEC 27001 Annex A Controls
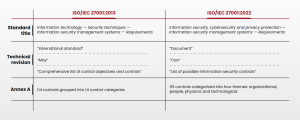
ISO/IEC 27001 was updated in 2022 to ensure that information security management systems based on it effectively address the ever-evolving security challenges. The revision mainly focused on Annex A, where its controls were restructured into four themes, and the number was reduced from 114 to 93 controls.
The four themes of the security controls of ISO/IEC 27001:2022 are:
- Organizational Controls
- Information Security Policies: Develop and implement comprehensive security policies.
- Incident Management: Have processes in place for reporting and responding to security incidents.
- People Controls
- Awareness and Training: Ensure employees understand security risks and practices
- Screening: Conduct background checks during recruitment.
- Physical Controls
- Secure Areas: Protect physical access to information processing facilities.
- Equipment Security: Prevent loss or damage to assets.
- Technological Controls
- Access Control: Restrict system access based on roles and responsibilities.
- Cryptography: Use encryption to protect sensitive data.
Benefits of ISO/IEC 27001 Certification
Obtaining the PECB ISO/IEC 27001 Certificate will prove that you have:
- Obtained the necessary expertise to support an organization to implement an Information Security Management System that complies with ISO/IEC 27001
- Understood the Information Security Management System implementation process
- Provide continual prevention and assessments of threats within your organization
- Higher chances of being distinguished or hired in an Information Security career
- Understood the risk management process, controls, and compliance obligations
- Acquired the necessary expertise to manage a team to implement an ISMS
- The ability to support organizations in the continual improvement process of their Information Security Management System
- Gained the necessary skills to audit organization’s Information Security Management System
How do I get started with ISO/IEC 27001 Training?
Interested in expanding your knowledge and advancing your skills on Information Security? PECB experts are here to ease the certification process and help you obtain PECB Certified ISO/IEC 27001 Credentials.
How the adoption of multiple standards helped Centiro
The well-known Swedish software company

Centiro is certified against multiple standards* on security and personal data protection including ISO/IEC 27001 Information Security, ISO/IEC 27032 Cybersecurity, ISO 22301 Business Continuity, and the GDPR.
PECB Certified ISO/IEC 27001 training courses available
Learn more about the Information Security Management System through attending the PECB ISO/IEC 27001 training courses. By clicking in one of the options below, you can find the training that best suits to you and your career.






